This week, three Compute Engine VMs in my Google Cloud project were compromised and briefly used for crypto mining—the VMs were hacked.
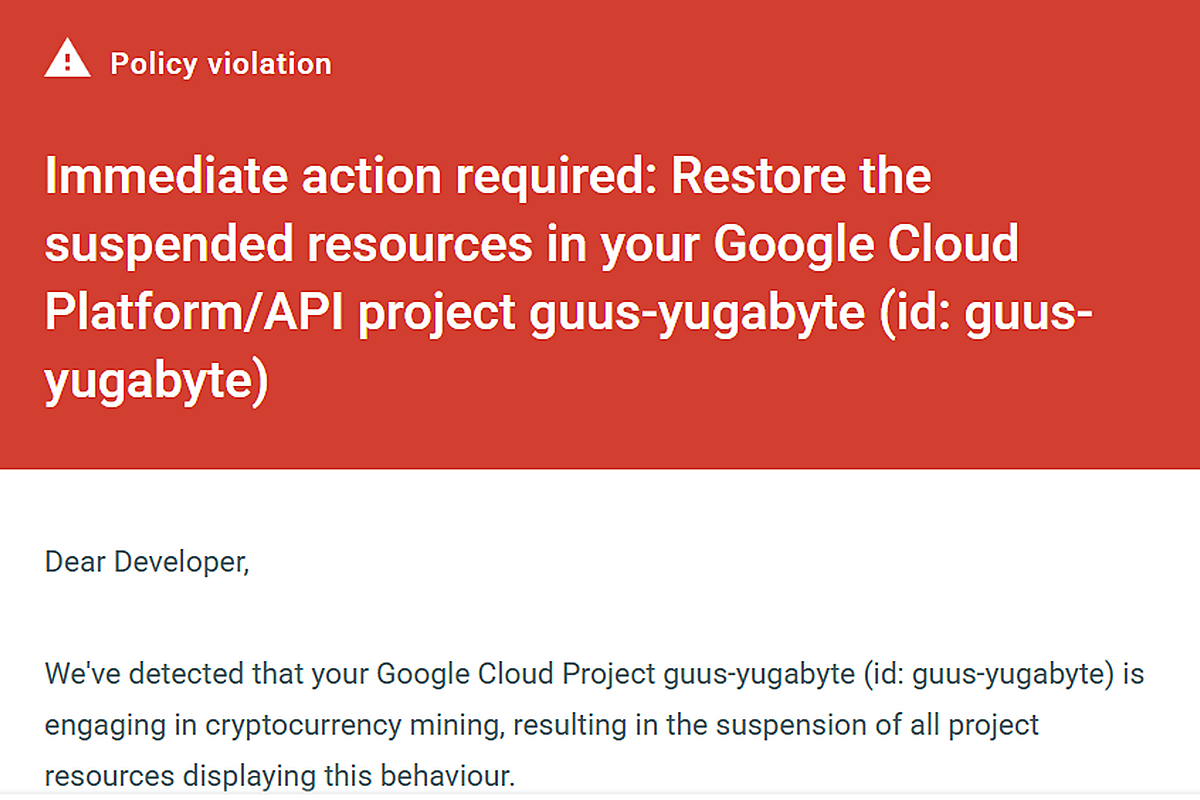
Google detected the activity automatically, suspended the instances, and sent me a notification. That was an interesting email to receive!
Vibe-coding a database cluster in Google Cloud
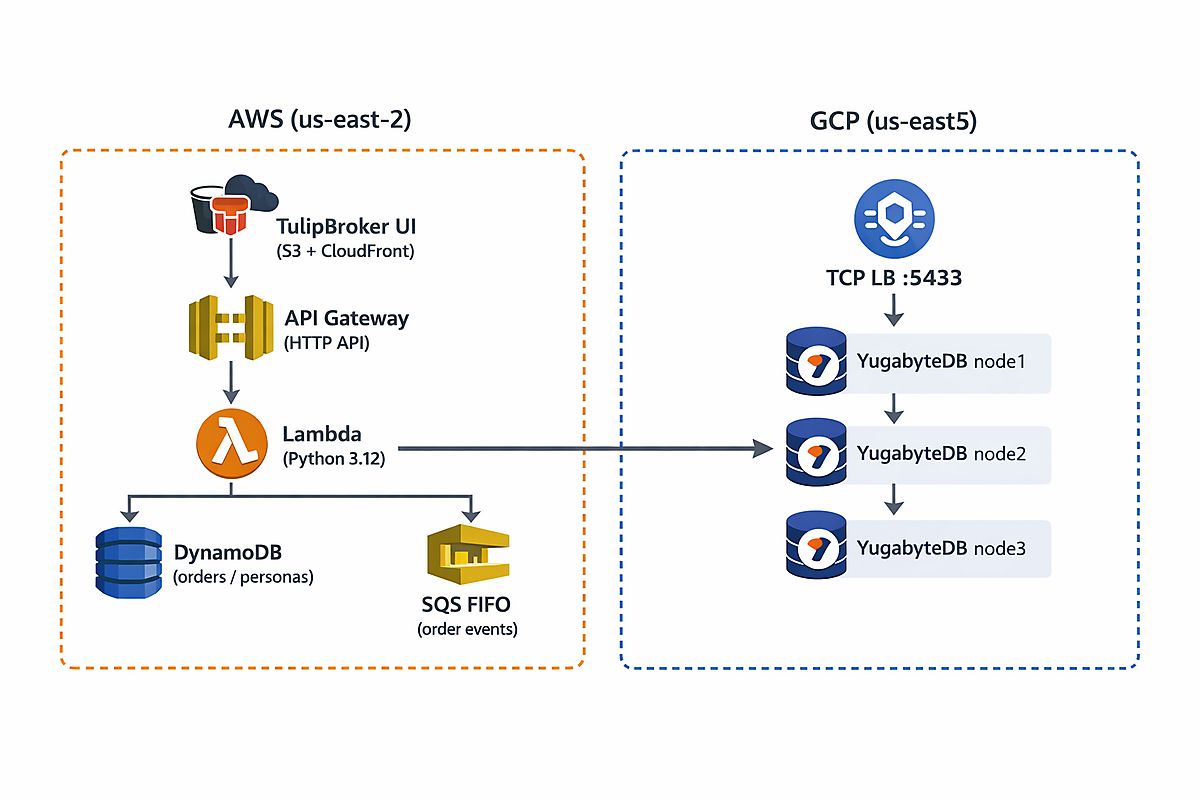
Last Sunday, I created three Ubuntu VMs in us-east5 to run a small YugabyteDB cluster. I wanted to test out some things with Yugabyte and also play with cross-cloud connectivity from an AWS application. After the experiment, I shut the VMs down because I was a little suspicious of leaving them running exposed to the internet. A good precaution, clearly.
Later in the week, I restarted them from my phone to demonstrate the setup to someone. Three hours later, CPU usage spiked, and GCP abuse detection sent me a notification. The Cloud Abuse logs flagged CRYPTO_MINING findings on all three instances, and monitoring showed that CPU went through the roof for these three machines.
It's pretty clear what happened—the VMs were internet-reachable and had multiple database/service ports exposed publicly, including Yugabyte. Some script must have detected the open ports, run an exploit, and installed the crypto mining software.
No harm done—all this is just a sandbox and I deleted the VMs. To be honest, like I wrote earlier, this is the best way to really experience the pro's and con's of agentic coding, and while it is a pretty obvious lesson for any cyber security professional, experiencing it so personally still feels differently.
I'll have my agentic assistant create a new cluster. This time, better protected!
Comment